- Microsoft Threat Modeling Tool Examples
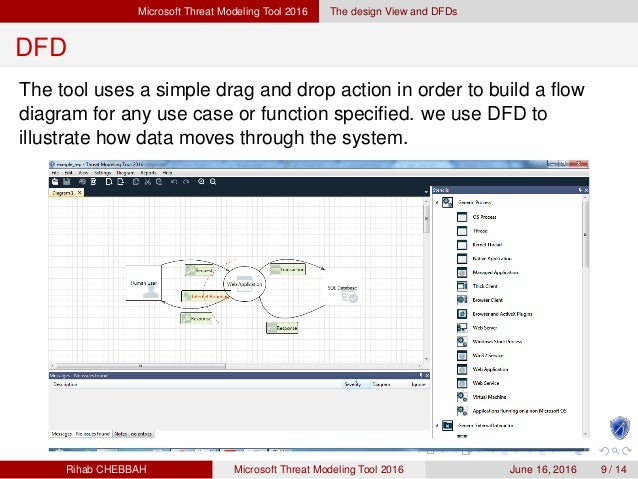
- Microsoft Threat Modeling Tool Uses Data Flow Diagram
- Microsoft Threat Modeling Tool Uses __ Threat Classification Scheme
- We are using Microsoft's Threat Modeling Tool 2016 (.TM7 format) and have found there to be no way to export the actual stencil into any format which we can graphically present. We have seen various other threads talking about being able to Copy/Paste from TMT over to Visio, but this was all for versions back in 2012 and later.
- Download and install Microsoft Threat Modeling Tool. Open the tool and choose.tb7 file in 'Template For new Models' field. Create A Model or open the example.
- Microsoft Threat Modeling Tool. Microsoft Threat Modeling Tool is one of the oldest and most tested threat modeling tools in the market. It is an open-source tool that follows the spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege (STRIDE) methodology.
Read Microsoft's privacy statement to learn more. Telemetry collection can be disabled by declining to participate in the customer experience improvement program during installation or at any time from the Settings- Options menu within the Threat Modeling Tool and deselecting 'Take part in anonymous customer experience improvement program.' Accelerating the resiliency threat modeling Program has already yielded many benefits for our critical Azure services, so we will be expanding this process to cover every service in Azure. To this end, we are continuously refining our process, documentation, and guidance as well as leveraging past risk discussions to address new risks. Ieee 1284 controller driver download.
-->The Threat Modeling Tool is a core element of the Microsoft Security Development Lifecycle (SDL). Osu mania mode download for mac. It allows software architects to identify and mitigate potential security issues early, when they are relatively easy and cost-effective to resolve. As a result, it greatly reduces the total cost of development. Also, we designed the tool with non-security experts in mind, making threat modeling easier for all developers by providing clear guidance on creating and analyzing threat models.
The tool enables anyone to:
- Communicate about the security design of their systems
- Analyze those designs for potential security issues using a proven methodology
- Suggest and manage mitigations for security issues
Here are some tooling capabilities and innovations, just to name a few:
- Automation: Guidance and feedback in drawing a model
- STRIDE per Element: Guided analysis of threats and mitigations
- Reporting: Security activities and testing in the verification phase
- Unique Methodology: Enables users to better visualize and understand threats
- Designed for Developers and Centered on Software: many approaches are centered on assets or attackers. We are centered on software. We build on activities that all software developers and architects are familiar with -- such as drawing pictures for their software architecture
- Focused on Design Analysis: The term 'threat modeling' can refer to either a requirements or a design analysis technique. Sometimes, it refers to a complex blend of the two. The Microsoft SDL approach to threat modeling is a focused design analysis technique
Next steps

The table below contains important links to get you started with the Threat Modeling Tool:See also: System requirements Remington gail typing test.
Microsoft Threat Modeling Tool Examples
| Step | Description |
|---|---|
| 1 | Download the Threat Modeling Tool |
| 2 | Read Our getting started guide |
| 3 | Get familiar with the features |
| 4 | Learn about generated threat categories |
| 5 | Find mitigations to generated threats |
Resources
Microsoft Threat Modeling Tool Uses Data Flow Diagram
Here are a few older articles still relevant to threat modeling today:
Microsoft Threat Modeling Tool Uses __ Threat Classification Scheme
Check out what a few Threat Modeling Tool experts have done:
Comments are closed.